Compliance statement
|
Collect
1. Scope of application and noun interpretation
Sensors Network Technology (Beijing) Co., LTD. (hereinafter referred to as "Sensors" or "We"), as the operator of the official website of Sensors and the software products and services of Sensors, always attaches great importance to the protection of users' personal information. In order to help enterprise customers using Sensors Software products (hereinafter referred to as "customers") better implement matters related to the protection of end user personal information, and to facilitate customers to better understand the compliance of Sensors Software products and the security protection technology capabilities that have been adopted, especially the methods and measures to protect personal information and privacy, Sensors has prepared this version of the Compliance Note. This note applies to all of our products and services and to specific software products and services that may be involved (hereinafter referred to as "our software products and services"), including but not limited to our official website,SDK1、API、Plugins, components, code, tools, and innovative software products (analytics, smart operations, smart recommendations, etc.) and services.
2. Description of data storage and application of Sensors software products
2.1. We solemnly promise not to access customer data without authorization
For users of Sensors software products that adopt the private deployment mode, that is, the system is deployed in the customer's computer room or the public cloud used by the customer (including but not limited to Alibaba Cloud, Tencent Cloud, Huawei Cloud, and Huawei Cloud).AWS、Azure .etc), related security measures and permission restrictions are controlled by the customer, and the data gods in the customer's computer room are not authorized to obtain them.
For adopting SaaS The user of the software product of the deployment mode, that is, the multi-node distributed deployment of the client system server, the user also has no right to contact the customer data, and the service resources are hosted only for service purposes.
We promise that in the process of providing software products and services, we will not contact relevant data or statistical results in the form of reports without the authorization of customers.
2.2. The software products and services provided by the Company may only be used for lawful purposes
Customers may use the software products and services for legitimate purposes only, and Customers need to ensure their use of the software软件Products and services Behavior conformityrelated to the provisions and regulatory requirements of laws and regulations do not infringe on the intellectual property rights and other legitimate rights and interests of any third party, and do not violate the provisions of legal documents binding on them. If the customer violates the above agreement, the company has the right to suspend provide products and services, and Upon termination of this Agreement, the service fee received will not be refunded;If the company is subject to third-party recourse, administrative investigation or other legal proceedings, the customer shall also compensate for all losses suffered by the company (including but not limited to the cost of responding to the lawsuit, the cost of cooperating with the investigation, the compensation of the third-party recourse, the attorney's fee, etc.).
In order to comply with the requirements of the Personal Information Protection Act on "obtaining the authorized consent of the right owner when collecting data", if the customer uses the software products for compliance data collection, it is required to disclose the third party in the User Privacy Note document SDK And mention of Sensors software products.
2.3. Disclaimer
If the customer uses the software products for data collection, it should ensure that the data source is legal and compliant, or has been authorized by the relevant parties and end users.
The customer's information processing of the end user shall be lawful and compliant, otherwise Shence has the right to request the customer to stop using Shence software products for data collection and processing, and reserves the right to pursue responsibility, and shall not be deemed as a breach of contract by Sensors.
If the customer uses the software products to collect and process the data of the third party designated by the customer, the third party demands and corresponding responsibilities arising from the behavior, the customer has the right to claim or compensate.
3. Sensors for data processing security protection measures
3.1. Data collection security
3.1.1. SDK Delayed initialization
3.1.1.1. Android Compliance steps
Android SDK Inv6.0.0 versions and above provide a way to delay initialization to meet compliance。Customers and its user agrees to the Privacy Policy after initialization SDK to collect data. You can refer to the following steps:
Calls for the first time after the agree with privacy policy called SensorsDataAPI. StartWithConfigOptions () to initialize the SDK, then in the Application of the onCreate () method of the main thread to initialize the SDK.
// Application 的 onCreate() 方法中主线程初始化 SDK if (同意隐私条款) { // 初始化配置 SAConfigOptions saConfigOptions = new SAConfigOptions(SA_SERVER_URL); // 开启全埋点 saConfigOptions.setAutoTrackEventType(SensorsAnalyticsAutoTrackEventType.APP_CLICK | SensorsAnalyticsAutoTrackEventType.APP_START | SensorsAnalyticsAutoTrackEventType.APP_END | SensorsAnalyticsAutoTrackEventType.APP_VIEW_SCREEN); // 其它初始化配置 // 初始化 SDK SensorsDataAPI.startWithConfigOptions(this, saConfigOptions); }// 在 Activity 中同意隐私条款后初始化 SDK if (未同意隐私条款) { //隐私协议弹窗相关逻辑 if(同意隐私条款) { // 初始化配置 SAConfigOptions saConfigOptions = new SAConfigOptions(SA_SERVER_URL); // 开启全埋点 saConfigOptions.setAutoTrackEventType(SensorsAnalyticsAutoTrackEventType.APP_CLICK | SensorsAnalyticsAutoTrackEventType.APP_START | SensorsAnalyticsAutoTrackEventType.APP_END | SensorsAnalyticsAutoTrackEventType.APP_VIEW_SCREEN); // 其它初始化配置 // 初始化 SDK,延迟初始化场景 context 需要传递 Activity SensorsDataAPI.startWithConfigOptions(this, saConfigOptions); } }- Deferred initialization only supports passing context as Activity for now.
- Disable initialization in onDestroy
- The Deeplink arousal page needs to be the same as the initialization page
- For the delayed initialization scenario, the triggered $AppStart event will not be able to carry static public attributes and will need to be usedAttribute plugins in advanced functionsto set properties in initialization.
If some buttons (such as a secure keyboard for entering a user password) contain private information, Android Buried Point provides an API to ignore the control's click event collection:
SensorsDataAPI.shareInstance().ignoreView(View view);Android SensorsFocus SDK Inv0.5.0 version and above provide a way to delay initialization to meet compliance。Customers and its user agrees to the Privacy Policy after initialization SDK. You can refer to the following steps:
Call for the first time after the agree with privacy policy called SensorsFocusAPI. StartWithConfigOptions (this, new SFConfigOptions (" pop-up window server address ")); Initializes the SDK, after which the main line initializes the SDK in the onCreate() method of the Application
// Application 的 onCreate() 方法中主线程初始化 SDK if (同意隐私条款) { // 初始化 SDK SensorsFocusAPI.startWithConfigOptions(this, new SFConfigOptions("弹窗服务端地址")); }// 在 Activity 中同意隐私条款后初始化 SDK if (未同意隐私条款) { //隐私协议弹窗相关逻辑 if(同意隐私条款) { SensorsFocusAPI.startWithConfigOptions(this, new SFConfigOptions("弹窗服务端地址")); } }- Deferred initialization only supports passing context as Activity for now
- Disable initialization in onDestroy
iOS Compliance steps
The Customer ensures that the user agrees to the Privacy Policy after the initial iOS SDK。
- (BOOL)application:(UIApplication *)application didFinishLaunchingWithOptions:(NSDictionary *)launchOptions { // Override point for customization after application launch. // 判断是否第一次打开 App,如果是进入隐私协议相关代码 if (<#第一次打开 App || 非第一次打开 App 但尚未同意用户协议#>) { // 隐私协议弹窗相关逻辑 if (<#同意用户协议#>) { // 初始化 SDK SAConfigOptions *options = [[SAConfigOptions alloc] initWithServerURL:SA_SERVER_URL launchOptions:launchOptions]; options.autoTrackEventType = SensorsAnalyticsEventTypeAppStart | SensorsAnalyticsEventTypeAppEnd | SensorsAnalyticsEventTypeAppClick | SensorsAnalyticsEventTypeAppViewScreen; [SensorsAnalyticsSDK startWithConfigOptions:options]; } }else{ // 初始化 SDK SAConfigOptions *options = [[SAConfigOptions alloc] initWithServerURL:SA_SERVER_URL launchOptions:launchOptions]; options.autoTrackEventType = SensorsAnalyticsEventTypeAppStart | SensorsAnalyticsEventTypeAppEnd | SensorsAnalyticsEventTypeAppClick | SensorsAnalyticsEventTypeAppViewScreen; [SensorsAnalyticsSDK startWithConfigOptions:options]; } ... return YES; }Certain buttons (such as the secure keyboard for entering a user password) contain private information, iOS Full Bury provides apis that can ignore the control's click event collection:
button.sensorsAnalyticesIgnoreView = YES;3.1.1.2. Web JS SDK Compliance steps
Web JS SDK 在 v1.21.1 Version and above provide a way to delay initialization to meet compliance。Customers and its user agrees to the Privacy Policy after initialization SDK to collect data. You can refer to the following steps:
<script> window.sensors_data_pre_config = { is_compliance_enabled: true } </script> <script charset='UTF-8' src="在 github 下载新版本的 sensorsdata.min.js "></script> if(同意隐私条款){ sensors.init({ server_url: 'http://test-syg.datasink.sensorsdata.cn/sa?token=xxxxx&project=xxxxxx', is_track_single_page:true, // 单页面配置,默认开启,若页面中有锚点设计,需要将该配置删除,否则触发锚点会多触发 $pageview 事件 use_client_time:true, send_type:'beacon', heatmap: { //是否开启点击图,default 表示开启,自动采集 $WebClick 事件,可以设置 'not_collect' 表示关闭。 clickmap:'default', //是否开启触达图,not_collect 表示关闭,不会自动采集 $WebStay 事件,可以设置 'default' 表示开启。 scroll_notice_map:'not_collect' } }); sensors.quick('autoTrack'); }- Set the window global variable sensors_data_pre_config before loading the Web JS SDK.
- The use of callback functions in the Web JS SDK API is not supported.
- Compliance does not support the asynchronous loading of the Web JS SDK.
3.1.1.3. Wechat mini program SDK compliance steps
Wechat mini program SDK Inv1.17.1 Version and above provide a way to delay initialization to meet compliance。Customers and the user agrees to the Privacy Policy after initialization SDK to collect data. You can refer to the following steps:
Create and introduce the config configuration file based on the following code to configure whether users are required to handle the user privacy Agreement
// config.js 文件 var sensors_data_pre_config = { is_compliance_enabled: true } // global 是微信小程序运行环境中提供的一个全局对象,需要给此全局对象设置 sensors_data_pre_config 属性 global.sensors_data_pre_config = sensors_data_pre_config; module.exports = sensors_data_pre_config;In app.js, before the introduction of Sensors wechat mini program SDK file, the config.js file should be introduced first (make sure that config.js is introduced before the introduction of Sensors wechat mini program SDK, if the customer will introduce other files before the introduction of Sensors wechat mini program SDK, You can also put the identifier in config.js about setting the privacy protocol into its file code)
Before executing the init method of Sensors wechat mini program SDK, it is necessary to execute the relevant logic of the user privacy agreement first, that is, if the pop-up window shows that the user agrees to the privacy bar box, then the init method must be called after the customer clicks on the consent to the privacy terms to complete the Sensors SDK initialization
var pre_config = require('./utils/config.js'); var sensors = require('./utils/sensorsdata.js'); // 用户隐私协议相关处理逻辑处理 // ...... // 同意隐私协议 // 在客户同意用户隐私协议后再调用 setPara 配置 SDK,然后调用 init 完成 SDK 的初始化 if(同意隐私协议){ sensors.setPara({ server_url: 'xxx', // 初始化配置 }); // 在用户同意隐私协议后,调用此方法表示可以进行数据采集 & 暂存,此方法需要保证在所有神策 SDK 调用前调用 sensors.enableDataCollect(); sensors.init(); } 3.1.1.4. React Native Compliance steps
React Native Module v2.2.5 Versions and above provide a way to delay initialization to meet compliance。Customers在and the user agrees to the Privacy Policy after initialization SDK tocollect data. You can refer to the following steps:
// 程序入口初始化 SDK import sensors,{SAAutoTrackType} from 'sensorsdata-analytics-react-native' if (未同意隐私条款) { // 隐私协议弹窗相关逻辑 if (<#同意用户协议#>) { // 初始化 SDK sensors.init({ server_url:'数据接收地址', auto_track:SAAutoTrackType.START|SAAutoTrackType.END|SAAutoTrackType.CLICK|SAAutoTrackType.VIEW_SCREEN }) } else { // 初始化 SDK sensors.init({ server_url:'数据接收地址', auto_track:SAAutoTrackType.START|SAAutoTrackType.END|SAAutoTrackType.CLICK|SAAutoTrackType.VIEW_SCREEN }) }3.1.2. SDK Local data encryption
3.1.2.1. Android SDK Compliance steps
Version requirement
Android SDK v6.2.0 version and above
The Android SDK provides encryption for cache content, which needs to be manually enabled. If there are requirements on the encryption method, the default encryption can not meet the requirements, you can realize custom encryption, custom encryption method can consult SDK students on duty.
Use the default encryption method
The Android SDK implements encryption by default, using AES encryption mode, AES 128 offset 16 bits, press the following code to enable encryption:
SAConfigOptions configOptions = new SAConfigOptions("数据接收地址"); //注册 MuPlugin 插件 configOptions.registerStorePlugin(new SAEncryptStorePlugin(this)); SensorsDataAPI.startWithConfigOptions(this, configOptions);Once compliant encryption or custom encryption is implemented,Encrypted data cannot be restored to unencrypted data
3.1.2.2. iOS SDK Compliance steps
Version requirement
iOS SDK v4.2.0 version and above
The iOS SDK provides encryption for cache content, which needs to be manually enabled. If there are requirements on the encryption method, the default encryption can not meet the requirements, you can realize custom encryption, custom encryption method can consult SDK students on duty.
Default Encryption Method
The iOS SDK implements encryption by default, using AES encryption with a 128-bit key and 16-bit offset. Just use the following code to enable encryption:
SAConfigOptions *options = [[SAConfigOptions alloc] initWithServerURL:<#数据接收地址#> launchOptions:launchOptions]; //注册加密插件 SAAESStorePlugin *plugin = [[SAAESStorePlugin alloc] init]; [options registerStorePlugin:plugin]; [SensorsAnalyticsSDK startWithConfigOptions:options];let options = SAConfigOptions.init(serverURL: <#数据接收地址#>, launchOptions: launchOptions) //注册加密插件 let plugin = SAAESStorePlugin() options.register(plugin) SensorsAnalyticsSDK.start(configOptions: options)Once compliant encryption or custom encryption is implemented, encrypted data will not be able to be restored to unencrypted data
3.1.2.3. Web JS SDK Compliance Steps
Currently, the Web JS SDK saves cookies that contain user information and properties set by the register function. The cookie can be deeply encrypted to ensure security.
When using encryption, all pages utilizing the SDK must be the latest version. Otherwise, if some pages use encrypted cookies and others use an older version of the SDK without decryption capabilities, it will lead to an inability to parse the cookies, resulting in the generation of new users that cannot be unified.
Version Requirements
- Web JS SDK v1.16.10 and above
Function Configuration
<script charset="UTF-8"> var sensors = window["sensorsDataAnalytic201505"]; // 初始化SDK sensors.init({ server_url: "数据接收地址", // 开启 cookie 加密配置,默认 false encrypt_cookie: true }); sensors.quick("autoTrack"); </script>3.1.2.4. Mini Program SDK Compliance Steps
Currently, the SDK saves user information and properties set by the register function in storage. The data in storage can be deeply encrypted to ensure security.
Version Requirements
- WeChat Mini Program SDK v1.14.9 and above
Function Configuration
// app.js var sensors = require('sensorsdata.min.js'); sensors.setPara({ name: 'sensors', server_url: '数据接收地址', encrypt_storage : true // 是否开启本地加密存储 });3.1.3. App Store Privacy Guidelines
For issues related to App Store submission, please refer to: https://manual.sensorsdata.cn/sa/latest/tech_sdk_client_app_store_compliance-41845311.html
3.2. SensorsData Information Desensitization Instructions
3.2.1. Encrypt specified display information
In the Sensors Analytics product, the display information can be configured based on roles, and corresponding encrypted user properties and event properties can be configured for each role. It can effectively desensitize important information without affecting the analysis.
Configuration reference document link: https://manual.sensorsdata.cn/sa/latest/guide_role-41844972.html#id-.成员与角色v2.3-指定加密信息
3.3. Sensors Data Destruction Security Instructions
3.3.1. It supports the EU General Data Protection Regulation (GDPR) and can delete underlying user data.
- Solution 1: Use the sa_clean data cleaning tool to delete the data
Configuration reference document link: https://manual.sensorsdata.cn/sa/latest/en/guide_role-185867020.html#id-.%E6%88%90%E5%91%98%E4%B8%8E%E8%A7%92%E8%89%B2v2.3-%E6%8C%87%E5%AE%9A%E5%8A%A0%E5%AF%86%E4%BF%A1%E6%81%AF
- Solution 2: Contact Sensors Data staff to delete the data after customer authorization confirmation.
If data deletion is required, the customer can contact Sensors Data staff and after customer authorization confirmation, the staff can assist the customer in deleting the data.
4. Sensors Data SDK Attribute Collection Compliance Instructions
4.1. Sensors Data SDK Product Permission Instructions
4.1.1. Android SDK Product Permission Instructions
To ensure the normal collection of customer data, Android SDK requires the following system permissions:
Permission | Usage | Required |
|---|---|---|
INTERNET | Allows the application to send statistical data | Required permission, SDK requires this permission to send event data |
ACCESS_NETWORK_STATE | Allows the application to detect network status | Must-have permission, the SDK will choose whether to send data based on the network status |
READ_PHONE_STATE | Allow the application to get the device's IMEI | Optional permission, this permission is used when collecting the $carrier attribute for in-app promotion and collection |
ACCESS_WIFI_STATE | Allow the application to get the MAC address | Optional permission, this permission is used for in-app promotion |
Although the Sensors Analytics Android SDK requires the above system permissions:
- The Android SDK will not request any permissions other than the above. If it is detected that a SDK with the same name as the Sensors Analytics SDK has requested permissions other than the above, please contact Sensors Analytics staff in a timely manner. Sensors Analytics will work with customers to investigate to avoid data security incidents.
- The Android SDK will not actively request authorization from the user. Sensors Analytics will inform customers of the above permissions when integrating the SDK, and customers need to call them themselves before initializing the SDK.
About Android ID: When collecting anonymized ID using the Android SDK, Android ID is commonly used to ensure accuracy. This method may have certain compliance risks. If customers do not need to use Android ID, they can disable the AndroidID interface by calling. If there are any other questions, please contact Sensors Analytics staff promptly.
Regarding OAID: When collecting anonymous IDs using the Android SDK, if the customer integrates the OAID SDK, in order to ensure accuracy, the OAID may be collected. If you have other questions, please contact Sensors Analytics staff in a timely manner.
4.1.2. iOS SDK Product Authorization Instructions
To ensure the normal collection of customer data, the iOS SDK requires the following system permissions:
Permission | Purpose | Required |
|---|---|---|
Network (Only for domestic use) | Allow the application to send data | Required permission, the SDK requires this permission to send event data |
Location | Allow the app to access GPS data | Optional permission, required for SDK to collect GPS data |
| IDFA | Allow the app to access IDFA | Optional permission, used for in-app promotion |
Although the Sensors Data iOS SDKrequiresthe above system permissions, but:
- The iOS SDK does not request permissions other than those mentioned above. If it is detected that an SDK with the same name as the Sensors Data SDK has requested permissions other than the above, please contact Sensors Data staff. Sensors Data will work together with the customer to investigate, to avoid data security incidents.
- Due to the characteristics of the iOS system, the iOS SDK may actively request user authorization, but only for the above permissions.
Explanation of IDFA: When the iOS SDK collects anonymous ID and performs channel matching, in order to ensure the accuracy of the collected data, IDFA is commonly used. This method may involve certain compliance risks; if customers do not need to collect IDFA, please remove the reference to the framework in the project and do not import the AdSupport related header files in the project. If you have any other questions, please contact Sensors Data staff in time.
4.2. SDK Collection, Data Sending, and Exception Handling Policies
See Android SDK & iOS SDK Security Guide for details.
4.3. Explanation of Predefined Attribute Data Collection by Sensors Data SDK
When using the SDK for data collection, the following predefined attributes are involved:
| Category | English Variable Name | Display Name | Data Type | Enabled Auto Collection | Whether Support Close | Default Whether Hide | Function(Analysis Technology Debug) | Information Privacy Risk Assessment | Risk Assessment Notes |
|---|---|---|---|---|---|---|---|---|---|
| Reserved Attributes | distinct_id | User ID | STRING | Yes | No | / | Analyze | No risk | |
| time | Time | DATETIME | Yes | No | / | Analyze | No risk | ||
| Basic Preset Attribute | $app_state | App State | STRING | Yes | No | Technology | Risk-free | ||
| $app_id | Application Unique Identifier | STRING | Yes | No | No | Analyze | Risk-free | ||
| $app_name | Application Name | STRING | Yes | No | No | Analyze | Risk-free | ||
| $app_version | Application Version | STRING | Yes | No | No | Analyze | Low Risk | ||
| $is_first_day | First Day Visit | BOOL | Yes | No | No | Analyze | Low Risk | Server-based secondary correction | |
| $is_first_time | Whether the event is triggered for the first time | BOOL | Yes | Yes | No | Analysis | Low risk | Secondary correction performed by the server | |
| $timezone_offset | Time zone offset | NUMBER | Yes | No | No | Analysis | Low risk | ||
| $event_duration | Event duration | NUMBER | is | is | no | analysis | low risk | ||
| $latitude | latitude | NUMBER | no | yes | no | analysis | high risk | ||
| $longitude | longitude | NUMBER | no | yes | No | Analysis | High risk | ||
| $title | Page title | STRING | Yes | Yes | No | Analysis | Low risk | ||
| $screen_name | Page name | STRING | Yes | Yes | No | Technology | Low Risk | ||
| app_crashed_reason | Crash Reason | STRING | No | Yes | No | Debug | No Risk | ||
| $url | Page Address | STRING | No | No | No | Analyze | Low Risk | ||
| $url_query | Page Parameter | STRING | Yes | Yes | No | Analysis | Low Risk | ||
| $url_path | Page Path | STRING | Yes | Yes | No | Analysis | Low Risk | ||
| $referrer | Referring Address | STRING | is | is | no | analysis | medium risk | ||
| $referrer_host | referrer domain | STRING | yes | yes | no | analysis | medium risk | ||
| $referrer_title | referrer page title | STRING | no | Yes | No | Analysis | No Risk | ||
| $user_agent | UserAgent | STRING | No | Yes | Yes | Technology | Medium Risk | ||
| $scene | Launch Scene | STRING | Yes | Yes | No | Analyze | Low Risk | ||
| $share_depth | Number of Shares | NUMBER | Yes | Yes | No | Analyze | Medium Risk | ||
| $share_distinct_id | Sharer | STRING | Yes | Yes | No | Analyze | Medium Risk | ||
| $share_url_path | Share Path | STRING | Yes | Yes | No | Analysis | Low Risk | ||
| $share_method | Share Method | STRING | Yes | Yes | No | Analysis | Low Risk | ||
| $source_package_name | Source Application Package Name | STRING | Yes | Yes | No | Analyze | Medium Risk | ||
| $bot_name | Spider name | STRING | Yes | Yes | No | Analyze | Low Risk | ||
| $viewport_height | Viewport Height | NUMBER | No | Yes | No | Analysis | Low Risk | ||
| $viewport_position | Position from the top of the viewport | NUMBER | No | Yes | No | Analysis | Low Risk | ||
| $viewport_width | Viewport width | NUMBER | No | Yes | No | Analysis | Low Risk | ||
| $item_join | Item Match Mode | - | No | Yes | No | Technical | No Risk | ||
| $receive_time | $receive_time | NUMBER | Yes | No | Yes | Technical | Risk-free | ||
| $lib_plugin_version | SDK plugin version | LIST | Yes | No | Yes | Technology | Risk-free | ||
| Device-related | $brand | Device brand | STRING | Yes | No | No | Analysis | Medium risk | |
| $manufacturer | Device Manufacturer | STRING | Yes | No | No | Analyze | Medium Risk | ||
| $model | Device Model | STRING | Yes | No | No | Analyze | Medium Risk | ||
| $os | Operating System | STRING | Yes | No | No | Analysis | Medium Risk | ||
| $os_version | Operating System Version | STRING | Yes | No | No | Analysis | Medium Risk | ||
| $screen_height | Screen Height | NUMBER | Yes | No | No | Analysis | Low Risk | ||
| $screen_width | Screen Width | NUMBER | Yes | No | No | Analysis | Low Risk | ||
| $wifi | Whether WIFI | BOOL | Yes | No | No | Analysis | Low Risk | ||
| $carrier | Carrier | STRING | Yes | No | No | Analysis | Medium Risk | Android SDK v6.8.0 and above are no longer collected | |
| $network_type | Network Type | STRING | Yes | No | No | Analysis | Low risk | ||
| $device_id | Device ID | STRING | No | No | No | Analyze | High risk | ||
| $screen_orientation | Screen Orientation | STRING | No | No | No | Analyze | Low risk | ||
| Browser-related | $browser | Browser | STRING | Yes | No | No | Analysis | Medium risk | |
| $browser_version | Browser version | STRING | Yes | No | No | Analysis | Medium risk | ||
| Click event-related | $element_id | Element ID | STRING | Yes | Yes | No | Technology | Low Risk | |
| $element_name | Element Name | STRING | Yes | Yes | No | Technology | Low Risk | ||
| $element_type | Element Type | STRING | YES | YES | No | Technology | Low-risk | ||
| $element_content | Element Content | STRING | Yes | Yes | No | Analysis | Low-risk | ||
| $element_position | Element Position | STRING | Yes | Yes | No | Technology | Low risk | ||
| $element_selector | Element selector | STRING | No | Yes | No | Technical | Low Risk | ||
| $element_target_url | Element Link URL | STRING | Yes | Yes | No | Technology | Low Risk | ||
| $element_class_name | Element Class Name | STRING | Yes | Yes | No | Technology | Low Risk | ||
| Latest Related Attribute | $latest_referrer | Last Referring URL | STRING | Yes | Yes | No | Analyze | Risk Medium | |
| $latest_referrer_host | Last Referring Domain | STRING | Yes | Yes | No | Analyze | Risk Medium | ||
| $latest_search_keyword | Last Search Engine Keyword | STRING | Yes | Yes | No | Analyze | Risk Medium | ||
| $latest_traffic_source_type | Latest Traffic Source Type | STRING | Yes | Yes | No | Analysis | Medium Risk | ||
| $latest_landing_page | Latest Landing Page | STRING | Yes | Yes | No | Analysis | Medium Risk | ||
| $latest_utm_campaign | Latest UTM Campaign Name | STRING | YES | YES | No | Analysis | Medium Risk | ||
| $latest_utm_content | Latest UTM Content | Metric | Yes | Yes | No | Analysis | Medium Risk | ||
| $latest_utm_medium | Latest UTM Medium | STRING | Yes | Yes | No | Analysis | Medium risk | ||
| $latest_utm_source | Latest ad campaign source | STRING | Yes | Yes | No | Analysis | Medium risk | ||
| $latest_utm_term | Latest ad campaign term | STRING | Yes | Yes | No | Analysis | High Risk | ||
| $latest_scene | Last Launch Scene | STRING | Yes | Yes | No | Analysis | Low Risk | ||
| $latest_share_method | The method of the latest share | STRING | Yes | Yes | No | Analysis | Low Risk | ||
| SDK Related | $lib | SDK Type | STRING | Yes | No | No | Debug | Non-risk | |
| $lib_version | SDK Version | STRING | Yes | No | Yes | Debug | Non-risk | ||
| $lib_method | Event Tracking Method | STRING | Yes | No | Yes | Debug | Safe | ||
| $lib_detail | Event Tracking Detail | STRING | Yes | Yes | Yes | Debug | Safe | ||
| Channel Related | $ios_install_source | Device fingerprint information required for App channel matching | STRING | No | Yes | / | Tech | High risk | Attribute not stored Attribute deleted after channel matching on the server side |
| $channel_device_info | Device fingerprint information required for App channel matching (Different from the event variable name above) | STRING | No | Yes | / | Tech | High risk | Attribute not stored Attribute deleted after channel matching on the server side | |
| $ios_install_disable_callback | Whether or not to track callback | BOOL | No | Yes | No | Technology | Low Risk | ||
| $is_channel_callback_event | Whether or not to perform channel matching callback | BOOL | No | Yes | Yes | Technology | Low Risk | ||
| $channel_extra_information | Channel extra information | STRING | No | Yes | Yes | Technology | High risk | ||
| $utm_matching_type | Channel tracking matching mode | STRING | No | Yes | No | Technology | Low risk | ||
| $utm_source | Advertising campaign source | STRING | No | Yes | No | Analyze | Medium Risk | ||
| $utm_medium | Advertising Campaign Medium | STRING | No | Yes | No | Analyze | Medium Risk | ||
| $utm_term | Advertising Campaign Keywords | STRING | No | Yes | No | Analyze | Medium Risk | ||
| $utm_content | Ad Campaign Content | STRING | No | Yes | No | Analyze | Medium Risk | ||
| $utm_campaign | Ad Campaign Name | STRING | No | Yes | No | Analyze | Medium Risk | ||
| $matched_key | Channel matching keyword | STRING | No | Yes | No | Technology | High risk | ||
| $matching_key_list | Channel matching keyword list | STRING | No | Yes | Yes | Technology | High risk | ||
| $short_url_key | Short URL Key | STRING | No | Yes | No | Technology | Low Risk | ||
| $short_url_target | Short Link Target URL | STRING | No | Yes | No | Technology | Low Risk | ||
| $channel_active_period_day | Effective Activation Window (days) | NUMBER | Yes | No | No | Analysis | No risk | ||
| $channel_callback_period_day | Depth Return Attribution Window (Days) | NUMBER | Yes | No | No | Analysis | No risk | ||
| $channel_attribute_period_hour | Activation Attribution Window (Hours) | NUMBER | Yes | No | No | Analyze | No risk | ||
| $channel_name | Channel Name | STRING | Yes | No | No | Analyze | No risk | ||
| $channel_account_id | Channel Account ID | STRING | Yes | No | Yes | Analyze | No risk | ||
| $channel_campaign_id | Channel Campaign ID | STRING | Yes | No | Yes | Analyze | No Risk | ||
| $channel_adgroup_id | Channel Adgroup ID | STRING | Yes | No | Yes | Analysis | Risk-free | ||
| $channel_ad_id | Channel Advertising Creative ID | STRING | Yes | No | Yes | Analysis | No Risk | ||
| $channel_click_id | Channel Tracking Click ID | STRING | Yes | No | No | Analysis | No Risk | ||
| $first_channel_name | First Channel Name | STRING | Yes | No | No | Analysis | No Risk | ||
| $first_channel_account_id | First Channel Account ID | STRING | Yes | No | Yes | Analysis | No Risk | ||
| $first_channel_campaign_id | First Channel Campaign ID | STRING | Yes | No | yes | analysis | no risk | ||
| $first_channel_adgroup_id | First Channel Adgroup ID | STRING | yes | no | yes | analysis | no risk | ||
| $first_channel_ad_id | First Channel Ad Creative ID | STRING | yes | no | yes | analysis | Risk-free | ||
| $first_channel_click_id | First Channel Click ID | STRING | Yes | No | No | Metric | User Segment | ||
| $channel_active_result | Channel Active Indicator | BOOL | Yes | No | No | Metric | User Segment | ||
| IP Related | $ip | IP | STRING | Yes | No | No | Technology | No risk | √(Nginx parsing) |
| $city | City | STRING | Yes | No | No | Analysis | No risk | √(Based on IP parsing) | |
| $province | Province | STRING | Yes | No | No | Analysis | No risk | √(based on IP resolution) | |
| $country | Country | STRING | Yes | No | No | Analysis | No risk | √(based on IP resolution) | |
| $ip_isp | IP Service Provider | STRING | yes | no | no | analysis | no risk | √(based on IP resolution) | |
| user association related | $is_login_id | Is Login ID | BOOL | yes | no | yes | technology | low risk | √(added when event is stored) |
| $track_signup_original_id | Associated Original ID | STRING | yes | No | No | Technology | No risk | ||
| item related preset attributes | $is_valid | Whether banned | BOOL | √ | |||||
| $receive_time | Arrival time | NUMBER | √ | ||||||
| $update_time | Update Time | DATETIME | √ |
- All the preset attributes involve more than 100. The above table lists the commonly collected preset attributes. If you need to view all the preset attributes, please contact the support staff of Sensors Analytics.
- Sensors Analytics SDK provides multiple interfaces for calling to meet the customer's requirements of turning off specific attribute collection. If you need to avoid the risks brought by $ios_install_source, you can choose the following methods:
- Method 1: Avoid using the channel tracking function, and do not call "activation event" and "channel information event".
- Method 2: Disable IMEI
For more detailed information, please contact the staff of Sensors Analytics.
4.4. Information Privacy Risk Assessment Grading Criteria Description
From: National standard GB/T 35273-2020 "Information Security Technology Personal Information Security Code"(hereinafter referred to as the "Specification")
References in the above specification to"personal information”,Information recorded electronically or otherwise capable of identifying, individually or in combination with other information, a particular natural person or reflecting the activities of a particular natural person, Such as name, date of birth, ID number, personal biometric information, address, communication contact information, communication records and contents, account password, property information, credit information, whereabouts, accommodation information, health and physiological information, transaction information, etc.
To determine whether a piece of information is personal information,Refer to the following two aspects:One is identification, that is, from information to individuals, a specific natural person is identified by the particularity of the information itself, and personal information should help to identify a specific individual. The second is the association, that is, from the individual to the information, such as a known specific natural person, the information generated by the specific natural person in its activities (such as personal location information, personal call records, personal browsing records, etc.) is personal information. Information that meets either of the above two circumstances shall be considered personal information.
表 A.1 Examples of personal information.
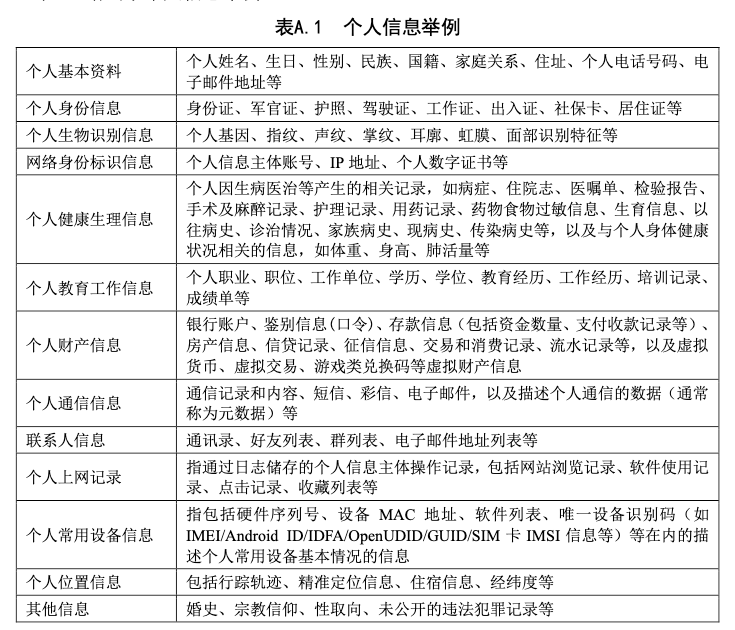
Sensitive personal information refers to personal information that, if leaked, illegally provided or abused, may endanger personal and property safety, easily lead to personal reputation, physical and mental health damage or discriminatory treatment. Under normal circumstances, the personal information of children under 14 years of age and information involving the privacy of natural persons are personally sensitive information. You can determine whether it is personal sensitive information from the following perspectives:
Divulge:Once personal information is leaked, it will cause the personal information subject and the organizations and institutions that collect and use personal information to lose their ability to control personal information, resulting in the spread of personal information and the use of uncontrollable. If some personal information is used directly or associated with other information in a manner contrary to the will of the personal information subject after being leaked, it may bring significant risks to the rights and interests of the personal information subject and should be judged as personal sensitive information. For example, the copy of the identity card of the personal information subject is used by others for real-name registration of the mobile phone number card, bank account opening card, etc.
Illegal offering:Some personal information may pose a significant risk to the rights and interests of the personal data subject only because it is spread outside the scope of authorization and consent of the personal data subject, and should be judged as personally sensitive information. For example, sexual orientation, deposit information, infectious disease history, etc.
Abuse:When some personal information is used beyond the authorized reasonable limits (such as changing the purpose of processing, expanding the scope of processing, etc.), it may bring significant risks to the rights and interests of the personal information subject, and should be judged as personal sensitive information. For example, health information is used by insurance companies for marketing and to determine the level of individual premiums without the authorization of the personal data subject.
表 B.1 个人敏感信息举例。

4.5. Custom property collection disclaimer
Information related to the business or the end user's own data is required by the customer Developer burying points through code (people writing data collection code)can collect, the SDK does not actively collect.
Customers should be guaranteed data sourcesLegal and compliant, or authorized by relevant parties and end users,to collect custom attribute data through our software products.
5. Sensors self-check instructions
5.1. Sensors SDK compliance description
Sensors SDK The only data type commonly collected is "Device ID",Mainly used for analysis。Customer needs collectionOther types of data,Need customersOn the basis ofbusinessrequirementAnd select the enabled SDK feature to make the corresponding selection:
Call -login: Interface: continue to select "User ID"
Open the full buried point: continue to select "Product interaction"
Enable crash collection: Continue to select "Crash Data"
- Enable collection of latitude and longitude: Continue to select "precise location"
Also, customers can update their privacy policies in a timely manner based on adjustments to their business.
Sensors Data complies with data-related laws and regulations in multiple countries.
According to self-inspection, Sensors Data software products comply with the requirements of "Basic Specifications for Mobile Internet Application (App) Collection of Personal Information (Draft)" and also comply with the European Union's General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) in the United States. In response to the above standards, Sensors Data SDK provides the following functions:
- Whether to start data collection after initialization
- Turn data collection on or off for the current app
- Disable collection of specific properties
- Disable collection of specific track events
- Disable collection of specific properties under specific track events
- The recognition ID of the current user, used for exporting data
- Function to delete specific user data
- Function to delete data based on interface/tools
5.1.1. Self-inspection results based on the "Network Security Law of the People's Republic of China"
According to self-inspection, the Sensors Data software products provided to customers (including SDK) do not violate the mandatory provisions of the "Network Security Law".
5.1.2. Self-inspection results based on the "Personal Information Protection Law of the People's Republic of China"
According to self-inspection, the Sensors Data software products provided to customers (including SDK) do not violate the mandatory provisions of the "Personal Information Protection Law".
5.1.3. Self-assessment based on Data Security Law of the People's Republic of China"
According to self-inspection, the Sensors Data software products provided to customers (including SDK) do not violate the mandatory provisions of the "Data Security Law".
6. Sensors Data Certification Explanation
6.1. Information Security Management Certification
Sensors Data has obtained the ISO 27001 Information Security Management System Certification ISO 27001
Sensors Data has obtained the ISO 27701 Privacy Information Management System Certification
Sensors Data has obtained the ISO 9001 Quality Management System Certification
Sensors Data has obtained the CMMI 3 Certification
Sensors Analytics Cloud, Sensors Marketing Cloud, and Sensors Ads Cloud have obtained Level 3 Network Security Protection Filing and Evaluation
6.2. Industry qualifications
Sensors Data actively practices data compliance and participates in various compliance activities in the industry.
On February 2020, Sensors Data was approved to establish the Working Group on Mobile Internet User Information Security Protection at the 6th China Internet Rule of Law Conference. It included 46 enterprises/institutions/ research institutions such as Sensors Data, Alibaba, ByteDance, Huawei, Baidu, and Xiaomi
In November 2020, the National APP Personal Information Protection Supervision Committee organized by the Ministry of Industry and Information Technology released 10 standards for the "APP User Rights Protection Evaluation Specification" and 8 standards for the "APP Collection and Use of Personal Information Minimum Necessary Assessment Specification". As a member of the Internet Association, Sensors Data's founder & CEO, San Wenfeng, read the "APP Personal Information Protection Public Commitment Letter" during the conference. The commitment letter is as follows:
6.3. 
6.4. Security Audit Reports
"Sensors Data Android SDK Source Code Security Audit Report"
"Sensors Data iOS SDK Source Code Security Audit Report"
"Sensors Data JS SDK Source Code Security Audit Report"
"Sensors Data WeChat Mini Program Source Code Security Audit Report"
"Sensors Data Privacy Policy"
Customers can contact Sensors Data's Customer Success/Project Manager to obtain the above security audit reports
7. Noun Explanation
1.SDK (Software Development Kit,Hereinafter referred to as SDK)The SDK provided by Shence includes but is not limited to Android SDK, iOS SDK, Web JS SDK, mini program SDK, mini game SDK, C SDK, C# SDK, Java SDK, etc. Preset attributes refer to the attribute information collected by the SDK.
Note: The content of this document is a technical document that provides details on how to use the Sensors product and does not include sales terms; the specific content of enterprise procurement products and technical services shall be subject to the commercial procurement contract.
 Popular Searches
Popular Searches